Database encryption software is a crucial tool in safeguarding sensitive information from unauthorized access. By implementing robust encryption techniques, organizations can ensure the security and integrity of their data. This article delves into the world of database encryption software, exploring its significance and functionality in today’s data-driven landscape.
From the various types of encryption methods to best practices for implementation, this comprehensive guide will provide valuable insights into how database encryption software works and the steps involved in securing valuable data assets.
Overview of Database Encryption Software
Database encryption software is a crucial tool used to protect sensitive data stored within databases by converting the information into a secure format that can only be accessed with the appropriate decryption key. This software plays a vital role in safeguarding information from unauthorized access, ensuring data confidentiality and integrity.
Purpose of Database Encryption Software
Database encryption software is designed to prevent unauthorized users from viewing or manipulating sensitive data stored in databases. By encrypting the information, the software adds an extra layer of security, making it difficult for cybercriminals or malicious insiders to access or steal valuable data.
- Encrypting data at rest and in transit
- Protecting against data breaches and cyber attacks
- Compliance with data protection regulations
Importance of Securing Sensitive Data Through Encryption
Securing sensitive data through encryption is essential to prevent data breaches, identity theft, and financial fraud. With the increasing number of cyber threats targeting databases, encryption software helps organizations mitigate risks and protect their reputation by ensuring that confidential information remains confidential.
- Preserving data confidentiality
- Maintaining data integrity
- Building customer trust
How Database Encryption Software Works
Database encryption software uses algorithms to transform plaintext data into ciphertext, making it unreadable without the decryption key. This process involves encrypting data before it is stored in the database and decrypting it when needed for authorized users to access. By implementing encryption, organizations can prevent unauthorized access and ensure that sensitive information remains secure.
Database encryption software employs strong encryption algorithms such as AES (Advanced Encryption Standard) to protect data from unauthorized access.
Types of Database Encryption
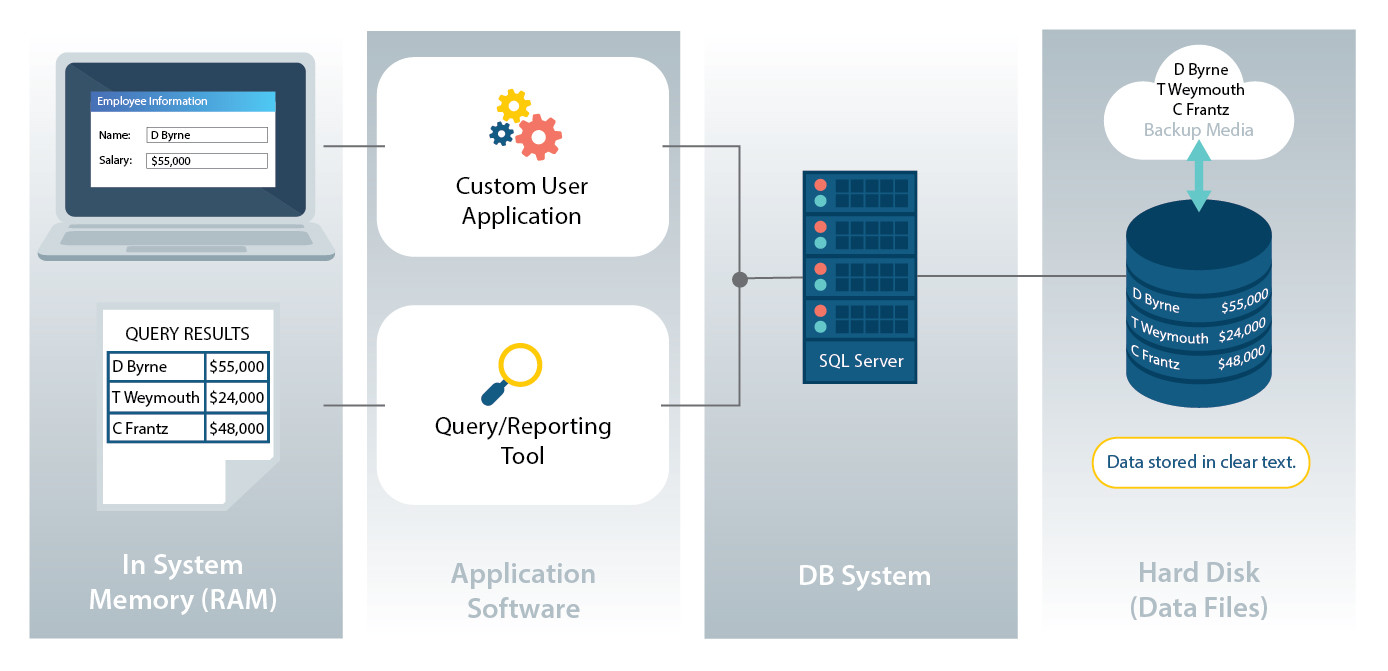
Database encryption software utilizes various encryption methods to secure sensitive information within databases. Two common types of encryption used are symmetric and asymmetric encryption, each with its own unique characteristics and advantages. Key management also plays a crucial role in ensuring the security and integrity of encrypted data.
Symmetric Encryption
Symmetric encryption, also known as secret key encryption, uses a single key to both encrypt and decrypt data. This key is shared between the sender and the recipient, making it faster and more efficient for encrypting large amounts of data. However, the main challenge with symmetric encryption is securely sharing and managing the encryption key to prevent unauthorized access.
Asymmetric Encryption
Asymmetric encryption, also called public key encryption, involves the use of a pair of keys – a public key for encryption and a private key for decryption. This method provides a higher level of security as the private key is never shared or exposed. While asymmetric encryption is slower compared to symmetric encryption, it is commonly used for secure communication and key exchange in databases.
Key Management in Database Encryption, Database encryption software
Key management is a critical component of database encryption as it involves securely generating, storing, and distributing encryption keys. Proper key management practices ensure that encryption keys are protected from unauthorized access and are regularly rotated to enhance security. Additionally, key management systems help track and audit key usage to maintain data integrity and compliance with security standards.
Features and Functionality

Database encryption software offers a range of features to enhance data security and protect sensitive information. Let’s explore some common functionalities and how encryption software integrates with databases.
Common Features of Database Encryption Software
- Encryption of Data: The primary function of encryption software is to encrypt data stored in databases, ensuring that it is protected from unauthorized access.
- Key Management: These tools provide robust key management systems to securely generate, store, and manage encryption keys used to protect data.
- Auditing and Logging: Database encryption software often includes auditing and logging capabilities to track access to encrypted data and monitor any suspicious activities.
- Compliance Support: Many solutions offer compliance support for regulatory requirements such as GDPR, HIPAA, or PCI DSS, helping organizations meet data protection standards.
- Granular Access Control: Encryption software allows organizations to implement granular access control policies, restricting access to sensitive data based on user roles and permissions.
Integration with Databases
Database encryption software seamlessly integrates with various database management systems (DBMS) like MySQL, Oracle, SQL Server, and others. These tools typically provide plugins or APIs that allow for easy integration with existing databases, ensuring minimal disruption to operations.
Enhancing Data Security with Encryption Software
By encrypting data at rest and in transit, database encryption software adds an extra layer of protection to prevent unauthorized access and mitigate the risk of data breaches.
Encryption software also helps organizations safeguard sensitive information from insider threats and external cyber-attacks, ensuring data confidentiality and integrity are maintained at all times.
Implementation and Best Practices: Database Encryption Software

When it comes to implementing database encryption software, there are several best practices that organizations should follow to ensure the security of their sensitive data.
Best Practices for Implementing Database Encryption Software
- Identify sensitive data: Before implementing encryption, it is crucial to identify the specific data that needs to be protected.
- Choose strong encryption algorithms: Select encryption algorithms that are widely recognized and considered secure to safeguard your data effectively.
- Implement key management: Proper key management is essential to ensure that encryption keys are securely stored and managed to prevent unauthorized access.
- Regularly update encryption software: Stay current with software updates and patches to address any security vulnerabilities and ensure the effectiveness of the encryption solution.
- Monitor and audit encryption processes: Regularly monitor and audit encryption processes to detect any anomalies or unauthorized access attempts.
Selecting the Right Encryption Software for Specific Database Needs
- Evaluate database compatibility: Choose encryption software that is compatible with your existing database systems to ensure seamless integration.
- Consider scalability: Select encryption software that can scale with your organization’s growing data needs and future requirements.
- Assess performance impact: Evaluate the performance impact of the encryption software on your database operations to minimize any slowdowns.
Challenges and Considerations when Deploying Encryption Software in Databases
- Key management complexity: Managing encryption keys can be complex, requiring careful planning and implementation to prevent data loss.
- Regulatory compliance: Ensure that the encryption software meets regulatory requirements and industry standards to avoid non-compliance issues.
- Data recovery: Implement robust data recovery processes to ensure that encrypted data can be recovered in case of system failures or data loss incidents.
Closing Summary
In conclusion, database encryption software plays a vital role in maintaining data privacy and preventing security breaches. By understanding the features, types, and best practices associated with this technology, organizations can enhance their overall data protection strategies and mitigate risks effectively.
FAQ Explained
What is database encryption software?
Database encryption software is a specialized tool designed to encode sensitive data stored in databases, ensuring that unauthorized users cannot access or decipher the information.
How does database encryption software enhance data security?
Database encryption software enhances data security by converting plaintext data into ciphertext, making it unreadable without the proper decryption key. This adds an extra layer of protection to sensitive information.
What are some common challenges in deploying encryption software in databases?
Some common challenges include key management, performance impact, compatibility issues with existing systems, and ensuring seamless integration with database operations.
