Blacklisting software, a crucial component in safeguarding digital assets, plays a pivotal role in identifying and blocking malicious content. As organizations strive to fortify their cybersecurity defenses, understanding the nuances of blacklisting software becomes imperative.
In this detailed exploration, we delve into the intricacies of blacklisting software, shedding light on its types, functionality, implementation, effectiveness, and limitations to provide a comprehensive understanding of its significance in the realm of cybersecurity.
Introduction to Blacklisting Software
Blacklisting software refers to a cybersecurity tool that blocks access to specific websites, applications, or IP addresses deemed harmful or malicious. Its primary purpose is to protect systems and networks from potential threats by preventing users from interacting with known dangerous entities.
Blacklisting software plays a crucial role in cybersecurity by providing an additional layer of defense against cyber attacks. By maintaining a list of unauthorized entities, it helps to minimize the risk of malware infections, data breaches, and other security incidents.
Examples of Industries Using Blacklisting Software
- Financial Institutions: Banks and financial organizations often utilize blacklisting software to safeguard sensitive financial data and prevent fraudulent activities.
- Government Agencies: Government entities rely on blacklisting software to protect classified information, critical infrastructure, and citizen data from cyber threats.
- Enterprises: Large corporations and businesses implement blacklisting software to secure their networks, devices, and confidential business information from cyber attacks.
Types of Blacklisting Software
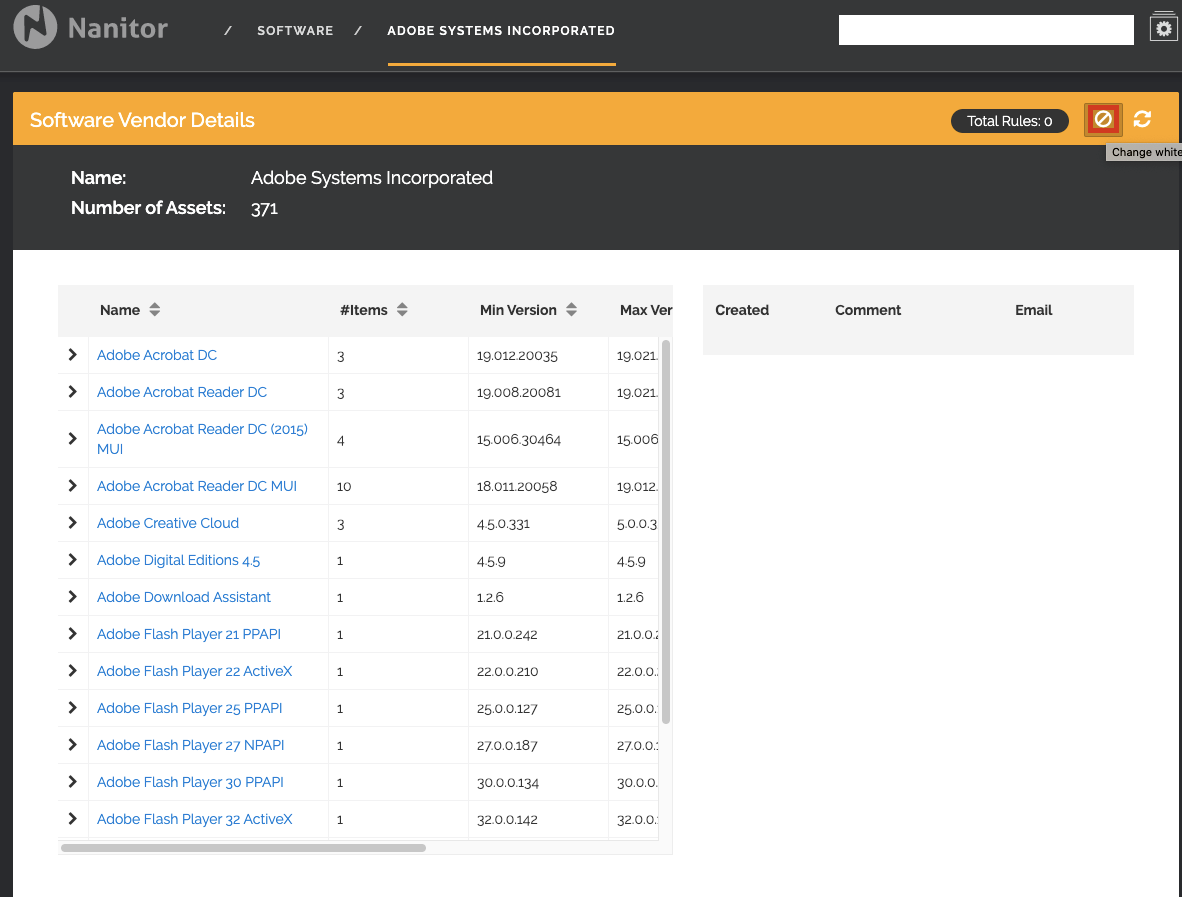
Blacklisting software comes in different types based on their scope and functionality. Two main categories include local blacklisting software and network-based blacklisting software.
Local Blacklisting Software
Local blacklisting software is installed on individual devices or systems to block access to specific websites, applications, or content. It is primarily used to restrict user access to potentially harmful or inappropriate content on a single device.
- Local blacklisting software is often used by parents to control their children’s internet usage and prevent them from accessing harmful websites.
- It can also be utilized by organizations to enforce internet usage policies and protect sensitive data on employee devices.
Network-Based Blacklisting Software
Network-based blacklisting software operates at the network level to block access to malicious websites, URLs, or IP addresses across an entire network. It provides centralized control and monitoring capabilities for multiple devices connected to the network.
- Network-based blacklisting software is commonly used by enterprises to protect their network infrastructure from cyber threats and malware attacks.
- It helps in preventing unauthorized access to malicious websites and phishing attempts targeting network users.
Categories of Threats Blacklisting Software Can Protect Against
Blacklisting software can protect against a wide range of threats, including:
- Malware: Blacklisting software can block access to websites known to distribute malware or host malicious files.
- Phishing: It can detect and block phishing websites designed to steal sensitive information from users.
- Ransomware: Blacklisting software can prevent users from accessing ransomware-infected websites or links.
- Botnets: It can block communication with command and control servers used by botnets to launch attacks.
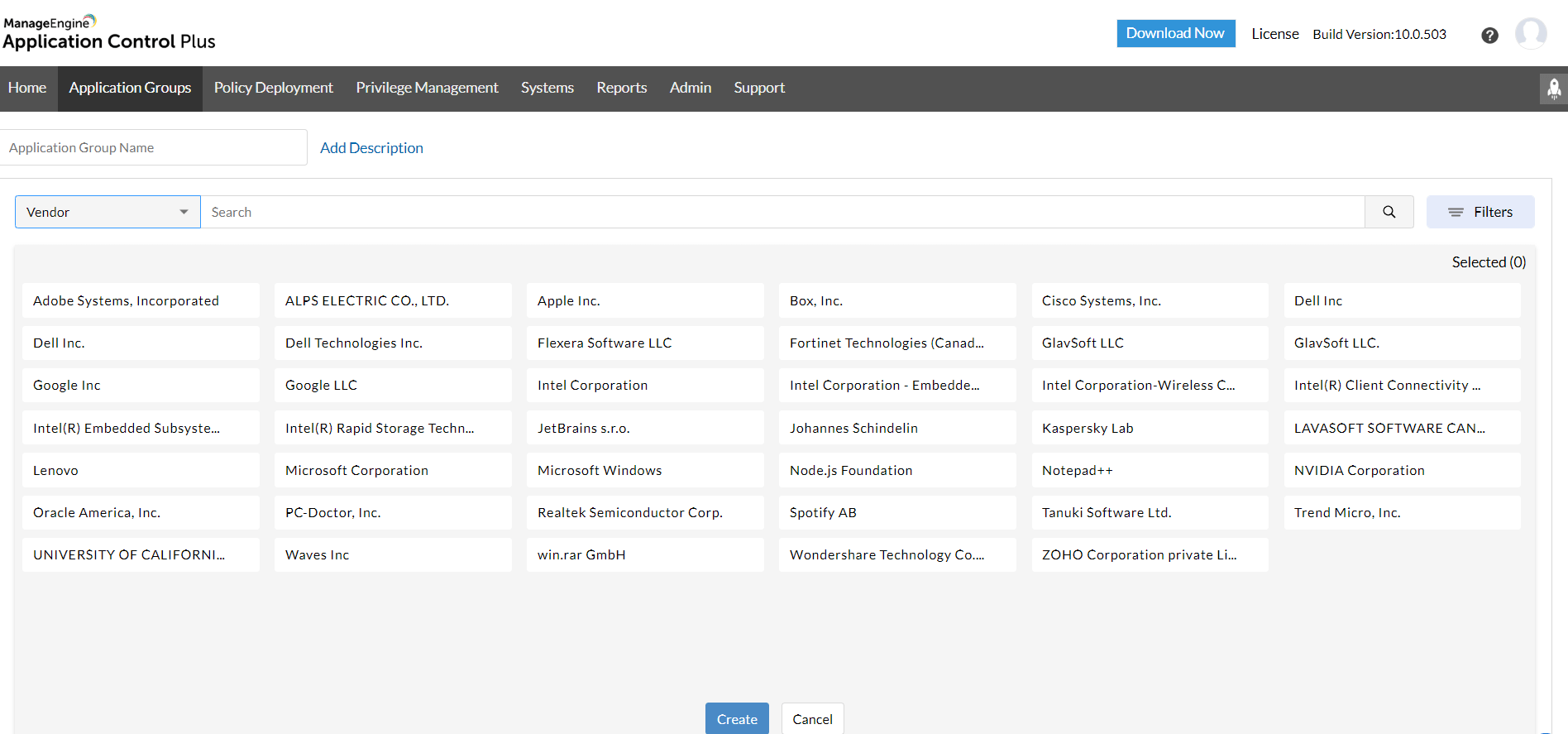
Difference Between Blacklisting and Whitelisting Software
Blacklisting software works by blocking known threats based on a predefined list of malicious entities, while whitelisting software allows only approved entities access based on a list of trusted sources. The key difference lies in their approach to managing access to resources, with blacklisting focusing on blocking threats and whitelisting focusing on allowing only approved entities.
Functionality of Blacklisting Software
Blacklisting software plays a crucial role in protecting systems and networks from cyber threats by identifying and blocking malicious content. This software utilizes various techniques to accomplish this, including scanning for known malware signatures, monitoring network traffic for suspicious patterns, and analyzing website reputation.
Identification and Blocking of Malicious Content
Blacklisting software identifies malicious content by comparing files, URLs, or IP addresses against a database of known threats. When a match is found, the software blocks access to the identified threat, preventing it from causing harm to the system or network. This proactive approach helps in mitigating the risk of cyberattacks.
Role of Databases in Blacklisting Software
Databases are essential components of blacklisting software as they store information about known threats, such as malware signatures, phishing URLs, and malicious IP addresses. By regularly updating these databases with new threat data, blacklisting software can effectively protect against emerging cyber threats and vulnerabilities.
Examples of Popular Blacklisting Software Tools
– Symantec Endpoint Protection: A comprehensive security solution that includes blacklisting capabilities to protect endpoints from malware and other threats.
– McAfee Web Gateway: An advanced web security gateway that uses blacklisting to block access to malicious websites and prevent data breaches.
– Palo Alto Networks WildFire: A threat intelligence platform that leverages blacklisting to identify and block known malware and zero-day threats in real-time.
Implementation of Blacklisting Software

Implementing blacklisting software on a network involves several key steps to ensure optimal security measures are in place. It is essential to follow best practices and address potential challenges that organizations may face during the implementation process.
Setting Up Blacklisting Software
When setting up blacklisting software, organizations should start by defining a clear policy outlining what websites, applications, or IP addresses are deemed unsafe or inappropriate. This policy should be communicated to all employees to ensure compliance.
- Install the blacklisting software on all devices connected to the network, including computers, mobile devices, and servers.
- Regularly update the blacklist with new threats and vulnerabilities to stay ahead of potential security risks.
- Configure the software to block access to specific websites or applications based on predefined criteria.
Configuring Blacklisting Software for Maximum Security
To maximize security, organizations should consider the following best practices when configuring blacklisting software:
- Enable real-time monitoring and alerts to quickly identify and respond to security threats.
- Implement strong password policies and access controls to prevent unauthorized changes to the blacklist.
- Regularly review and audit the blacklist to ensure it remains up-to-date and effective in blocking potential threats.
Challenges in Implementing Blacklisting Software
While blacklisting software can enhance security, organizations may face challenges during the implementation process:
- False positives: There is a risk of legitimate websites or applications being incorrectly blocked by the software, impacting productivity.
- Resource consumption: Blacklisting software may require significant resources to operate efficiently, leading to performance issues on the network.
- User resistance: Employees may resist the restrictions imposed by the blacklist, leading to potential workarounds or non-compliance.
Effectiveness and Limitations of Blacklisting Software
Blacklisting software plays a crucial role in preventing cyber threats by blocking known malicious entities from accessing systems. However, it also comes with its own set of limitations when it comes to detecting evolving security risks.
Effectiveness of Blacklisting Software
Blacklisting software can be highly effective in blocking known threats such as viruses, malware, and malicious websites. By maintaining a database of blacklisted entities, the software can quickly identify and prevent access to these known threats, thereby enhancing the overall security of a system.
Limitations of Blacklisting Software
- Blacklisting software relies on a database of known threats, which means it may struggle to detect new or emerging security risks that have not yet been identified and added to the blacklist.
- There is a possibility of false positives, where legitimate websites or applications are mistakenly blocked due to being incorrectly identified as malicious entities.
- Cybercriminals can bypass blacklisting measures by using techniques such as obfuscation or polymorphism to disguise their malicious activities and evade detection.
Strategies to Complement Blacklisting Software
- Implement whitelisting measures to allow only approved applications and websites to run on systems, complementing the blacklisting approach by focusing on known safe entities.
- Utilize behavior-based detection methods that analyze the actions and patterns of software or users to identify suspicious activities that may not be captured by blacklisting alone.
- Regularly update blacklists with new threat information and consider using threat intelligence feeds to stay informed about emerging security risks.
Final Conclusion
In conclusion, blacklisting software emerges as a formidable ally in the battle against cyber threats, offering a layer of protection that is indispensable in today’s digital landscape. By embracing the capabilities of blacklisting software and complementing it with other cybersecurity measures, organizations can bolster their defenses and safeguard their valuable data from evolving security risks.
Commonly Asked Questions
How does blacklisting software differ from whitelisting software?
Blacklisting software blocks known threats based on predefined criteria, while whitelisting software only allows approved entities to access the system.
What industries commonly use blacklisting software?
Industries such as finance, healthcare, and e-commerce frequently employ blacklisting software to protect sensitive data and mitigate cyber risks.
What are the best practices for configuring blacklisting software?
Regular updates, customized rulesets, and continuous monitoring are key practices to ensure optimal performance of blacklisting software.
